As 2024 comes to a close, it is crucial to reflect on the lessons learned, challenges faced, and advancements made in the field of physical security. This year saw significant shifts in the way organizations, governments, and individuals perceive and implement security measures. Emerging technologies, evolving threat landscapes, and geopolitical tensions all played a role in shaping the physical security landscape.
In this article, we explore the key physical security trends of 2024, analyze the common threats and risks faced, and provide insights into what the coming year may bring, including the growing significance of Crime Prevention Through Environmental Design (CPTED) principles.
Key Physical Security Trends in 2024
1. Integration of Physical and Cybersecurity
One of the most noticeable trends of 2024 was the convergence of physical and cybersecurity. With the rise of Internet of Things (IoT) devices, particularly in surveillance and access control systems, vulnerabilities in cybersecurity increasingly posed risks to physical security. For example, ransomware attacks on physical security infrastructure, such as smart locks and video surveillance systems, became more frequent.
Key takeaway: Security professionals must adopt a holistic approach that considers both physical and cyber threats as interlinked aspects of overall safety.
2. Advancements in AI-Powered Surveillance
Artificial Intelligence (AI) played a transformative role in video surveillance. AI-driven systems enhanced capabilities in detecting suspicious activities, recognizing individuals, and even predicting potential threats through behavioral analytics. However, concerns regarding privacy and ethical use of these technologies remained a significant issue.
Key takeaway: The balance between enhanced security and privacy compliance will remain a focal point moving forward.
3. Focus on Workplace Violence Prevention
With workplace violence incidents on the rise globally, organizations prioritized measures to safeguard employees. These included more robust access management, improved training programs, and the integration of early warning systems to detect potential threats.
Key takeaway: Comprehensive risk assessments and proactive training programs are essential in preventing workplace violence.
4. Increased Emphasis on Sustainability and CPTED
Sustainability and Crime Prevention Through Environmental Design (CPTED) principles became intertwined as organizations sought security measures that aligned with global environmental goals. CPTED principles—such as natural surveillance, territorial reinforcement, and access control—were increasingly incorporated into sustainable designs for urban planning, commercial developments, and even residential neighborhoods.
Examples included:
- Natural Surveillance: Using landscaping and lighting to maximize visibility in public areas, reducing opportunities for crime.
- Territorial Reinforcement: Designing physical spaces to foster a sense of ownership and deter unauthorized access, such as defined property boundaries and community-focused layouts.
- Access Control: Integrating physical barriers like fencing, gates, and bollards in a way that complements architectural aesthetics.
Key takeaway: The integration of CPTED into sustainability initiatives is not just a trend but a necessity, helping create safer and environmentally friendly communities.
Threat Trends in 2024
1. Insider Threats
Insider threats continued to dominate the risk landscape. Disgruntled employees, social engineering tactics, and poor access management protocols contributed to many security incidents. The overlap between insider threats and hybrid work environments amplified the challenges for security teams.
2. Geopolitical Tensions and Critical Infrastructure
Heightened geopolitical tensions increased the targeting of critical infrastructure, such as power grids, water facilities, and transportation networks. These attacks often combined cyber and physical elements, exemplifying the need for cross-functional security measures.
3. Climate-Related Risks
Natural disasters, exacerbated by climate change, posed threats to physical infrastructure. Security measures needed to account for severe weather events, from securing facilities against flooding to managing evacuation protocols. CPTED principles, such as defensible space and proper site planning, were increasingly applied to address climate risks in urban environments.
4. Public Spaces and Mass Gatherings
Public spaces and mass gatherings remained vulnerable to violent incidents, including active attacker situations and terror attacks. Security for these venues required greater emphasis on rapid response capabilities and crowd management strategies. CPTED principles, such as controlling pedestrian flow through thoughtful design and incorporating natural barriers, played a vital role in reducing vulnerabilities.
Common Areas of Physical Risk
1. Access Management
Despite advancements in technology, unauthorized access remained a persistent risk. Common vulnerabilities included poorly managed visitor access, unsecured entry points, and reliance on outdated lock-and-key systems.
2. Video Surveillance Gaps
While surveillance systems have become more sophisticated, gaps in coverage, insufficient storage capabilities, and inadequate monitoring persisted as vulnerabilities.
3. Emergency Preparedness
Many organizations struggled to maintain comprehensive emergency response plans. Limited training, lack of coordination with first responders, and outdated communication systems were frequent issues.
4. Design Flaws in Public Spaces
Design flaws in public and shared spaces emerged as a common area of risk. Poor lighting, obstructed sightlines, and lack of clear territorial markings contributed to increased vulnerability to crimes. These issues underscored the importance of incorporating CPTED principles during the planning and retrofitting phases of public and commercial developments.
Looking Ahead: Predictions for 2025
1. Wider Adoption of Biometric Systems
Biometric access management systems, such as facial recognition and fingerprint scanning, are likely to become more prevalent. These technologies offer enhanced security but will require careful implementation to address privacy concerns and mitigate false positives.
2. CPTED for Smart Cities
As urban areas embrace “smart city” initiatives, CPTED principles will be adapted to fit interconnected and data-driven environments. Smart lighting, integrated traffic management systems, and AI-enabled public safety networks are poised to redefine urban security. For instance, AI-powered streetlights could adjust their brightness based on pedestrian activity, enhancing natural surveillance.
3. Hybrid Security Models
The future lies in hybrid security models that combine physical barriers with advanced digital technologies. For instance, integrating drones for perimeter surveillance with AI-powered monitoring systems could enhance security coverage significantly.
4. Regulatory Changes and CPTED Guidelines
Governments are expected to introduce stricter regulations around data protection and privacy in security systems. Simultaneously, CPTED-specific guidelines may evolve, emphasizing community safety in the context of sustainable urban design.
5. Greater Emphasis on Training and Resilience
With threats becoming more unpredictable, training programs will focus on building organizational resilience. This includes not only physical security measures but also psychological preparedness, CPTED-informed crisis management strategies, and enhanced communication protocols.
Conclusion
The past year underscored the evolving nature of physical security, marked by technological advancements, new threat paradigms, and a growing emphasis on sustainability and CPTED principles. As we enter 2025, security professionals must remain agile, continuously learning and adapting to the dynamic risk landscape. By leveraging technology responsibly, incorporating CPTED into all phases of design, and fostering cross-functional collaboration, the physical security community can rise to meet the challenges ahead.
If your Municipality wants to learn more about this topic and read the full article version visit here. Feel free to contact me directly at michael@michaelwhitegroup.com for further assistance.


 Every municipality is at a different place in their journey, and that’s okay. They have differing levels of asset management maturity, differing data and information and different levels of organizational buy in and support. The best tip is to start where you are and reach out to your local communities of practice (yes they exist across the country, I am most familiar with Asset Management Ontario), the Canadian Network of Asset Managers, the Federation of Canadian Municipalities or any of the numerous asset management training partners across the country. Many have free tools to figure out where you are, your best next steps to gap fill, and tools to help you along that journey.
Every municipality is at a different place in their journey, and that’s okay. They have differing levels of asset management maturity, differing data and information and different levels of organizational buy in and support. The best tip is to start where you are and reach out to your local communities of practice (yes they exist across the country, I am most familiar with Asset Management Ontario), the Canadian Network of Asset Managers, the Federation of Canadian Municipalities or any of the numerous asset management training partners across the country. Many have free tools to figure out where you are, your best next steps to gap fill, and tools to help you along that journey.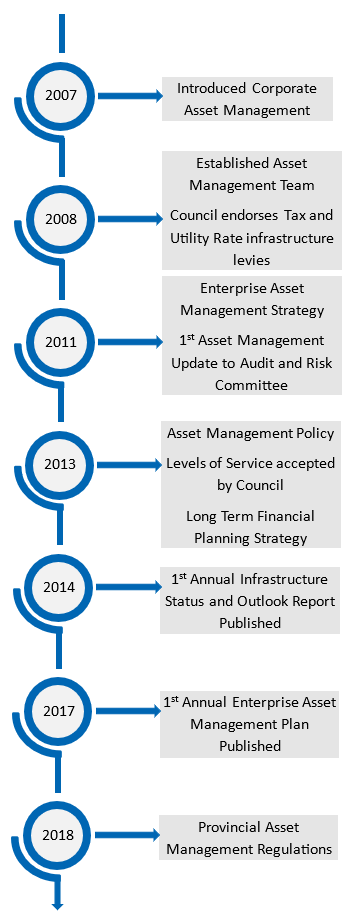 Enterprise Asset Management is an integral part of the Region of Peel’s strategic and long-term planning practices. Introduced in 2007, the program focuses on developing sustainable plans to maintain the infrastructure over a planning horizon that can be as long as 100 years. Guided by the principle of continuous improvement, these plans support Council’s level of service targets and long-term financial strategies. The Region’s Asset Management program is guided by industry best practice, as well as regulatory requirements. The program is continuously evolving to leverage opportunities and address challenges.
Enterprise Asset Management is an integral part of the Region of Peel’s strategic and long-term planning practices. Introduced in 2007, the program focuses on developing sustainable plans to maintain the infrastructure over a planning horizon that can be as long as 100 years. Guided by the principle of continuous improvement, these plans support Council’s level of service targets and long-term financial strategies. The Region’s Asset Management program is guided by industry best practice, as well as regulatory requirements. The program is continuously evolving to leverage opportunities and address challenges.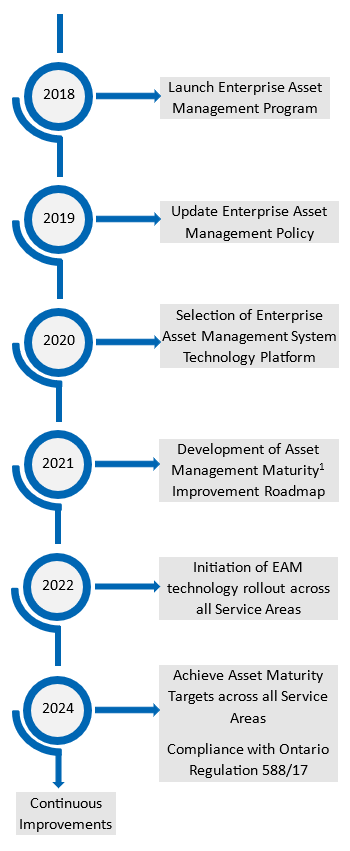








.png)





